Obtaining and Delivering SXG Files and the Challenges of Secondary Resource Prefetch.
As a Signed HTTP Exchanges (SXG) distribuidor, puede entregar archivos SXG en nombre de los creadores de contents original. Los browsers Web que admiten SXG mostrarán dichos archivos SXG como si fueran entregados por los creadores de contenido original. Esto le permite implementar la precarga entre sitios sin violar la privacidad. Esta guía le muestra cómo distribuir SXG correctamente.
Compatibility with various browsers
Actualmente, Chrome es el único browser que admite SXG. Consulte la sección Consenso y estandarización de HTTP exchanges signed by origin for the most up-to-date information.
Get SXG files
Specify in your Accept encabezado de solicitud que desea que el server devuelva un archivo SXG junto con la solicitud:
Accept: application/signed-exchange;v=b3,*/*;q=0.8This guide assumes that you place your SXG files in / var / www / sxg.
Serves a simple SXG file
Adjunte los siguientes headers para distribuir un solo archivo SXG:
Content-Type: application/signed-exchange;v=v3
X-Content-Type-Options: nosniffSet up nginx:
http {
...
types {
application/signed-exchange;v=b3 sxg;
}
add_header X-Content-Type-Options nosniff;location / {
more_set_headers "Content-Type: application/signed-exchange;v=b3";
alias /var/www/sxg/;
try_files $uri.sxg $uri =404;
autoindex off;
}
...
Upload the new configuration to nginx:
sudo systemctl restart nginx.servicenginx it will start serving SXG files. When Chrome accesses your server, the address of the original content publisher will appear in the bar.
Prior acquisition of secondary resources
La mayoría de las páginas web constan de múltiples subrecursos, como CSS, JavaScript, fuentes e imágenes. El contenido de SXG no se puede cambiar sin la clave privada del creador del contenido. Esto causa problemas cuando el navegador intenta resolver subrecursos.
For example, suppose index.html.sxg from https://website.test/index.html have a link to https://website.test/app.js. Cuando el navegador de un Username recibe el archivo SXG de https://distributor.test/example.com/index.html.sxg, you will find the link to https://website.test/app.js. The browser can retrieve https://website.test/app.js directly in the actual access, but should not be done in the preload phase to preserve privacy. If the resource was obtained during the preload phase, it would be possible for the content creator (website.test) to be able to detect which content distributor (distributor.test) is requesting the resource.
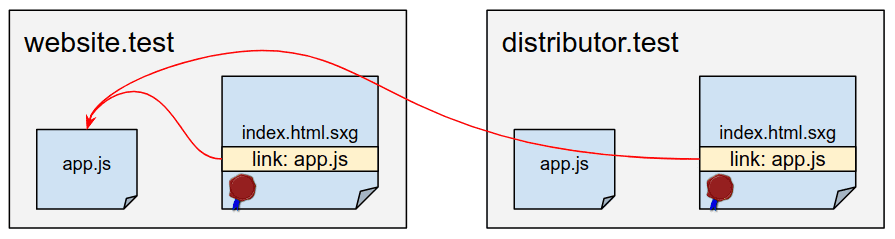
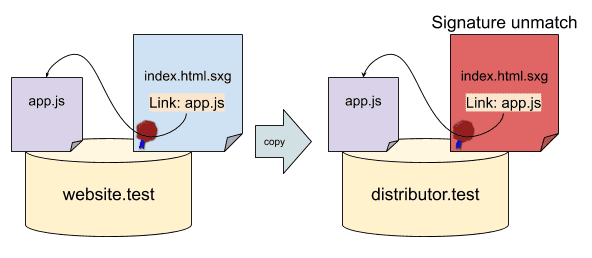
If the dealer wants to serve app.js.sxg of your own service and try to modify https://website.test/app.js to be the distributor version of that subresource (like https://distributor.test/website.test/app.js.sxg), provocará una discrepancia de firma y hará que el SXG no be válido.
To solve this problem, there is now an experimental SXG child resource pre-recovery feature in Chrome. You can enable it in: chrome://flags/#enable-sxg-subresource-prefetching. To use secondary resource prefetch, the following conditions must be met:
- The editor should embed a response header entry in SXG, like:
link: ; rel = "preload"; as = "script", ; rel = "allowed-alt-sxg"; header-integrity = "sha256-h6GuCtTXe2nITIHHpJM + xCxcKrYDpOFcIXjihE4asxk =". This specifies the subresource that can be substituted for the SXG-specific integrity hash. - The distributor must attach a response header when servicing the SXG, such as:
link: ; rel = "alternate"; type = "application / signed-exchange; v = b3"; anchor = "https: //website.test/app.js". This specifies the path ofapp.jsy corresponds to the subresource.
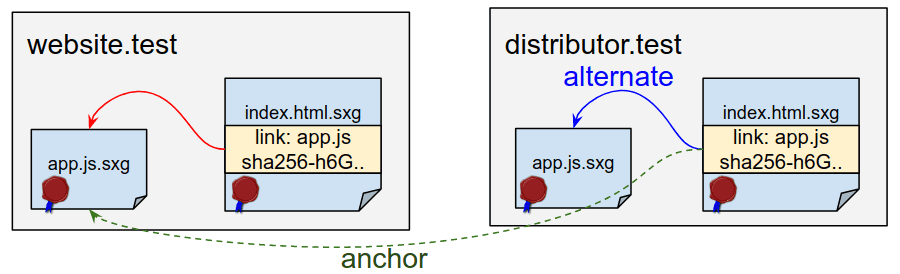
The first is relatively easy because nginx-sxg-module you can calculate integrity hashes and embed them in uplink reply link headers. But the second is more difficult because the content distributor must know the subresources specified in the SXG.
If there are no other additional resources than https://website.test/app.js, then all you need to add in your nginx config is:
add_header link <https://distributor.test/website.test/app.js.sxg>;rel="alter...But these cases are rare because typical websites consist of a large number of secondary resources. Additionally, the reseller must attach the appropriate anchor link header when delivering an SXG file. Currently, there is no easy way to solve this problem, so stay tuned for updates!
Post comments
Chromium engineers are eager to hear your comments on the SXG distribution at [email protected]. You can also join the specification discussionor Report a bug to the team. Your feedback will be of great help in the standardization process and will also help address implementation issues. Thanks!






