Me Blog, Leaving Work Behind, fue pirateado en abril. Es algo sobre lo que lees con bastante frecuencia pero que nunca esperas your hasta que be demasiado tarde. Para ser honesto, no me veía a mí mismo como un candidato principal: he escrito sobre la seguridad de WordPress con la suficiente frecuencia como para tener implementadas muchas medidas preventivas. A pesar de todo, esas medidas de forma clara no eran lo suficientemente completas.
Ser pirateado es algo por lo que no quiero volver a pasar. Hay tantas razones por las que el tiempo de inactividad de un sitio Web es malo para su blog / negocio: aún cuando la pérdida de traffic y los ingresos potenciales son los dos más obvios, no puedo subestimar la cantidad de tiempo que perdí para restaurar el sitio y la cantidad de estrés que genera. Me causó.
In this post, I want to reveal what happened to my site and let you know what I have done to increase the security of my site since then.
Getting hacked: my story
Me desperté el jueves 18 de abril y descubrí que mi sitio estaba caído y lo había estado durante unas horas. Inmediatamente me comuniqué con mi proveedor de alojamiento, Westhost, quien me informó que su firewall ModSecurity había detectado actividad inusual en mi sitio y lo había cerrado de inmediato como medida de precaución. Al ejecutar una restauración inicial en el sitio, pude ver de inmediato que había sido pirateado. Aún cuando los cambios fueron relativamente sutiles, estaba bastante claro que algunos tipos inescrupulosos habían estado husmeando.
It turns out that a large number of WordPress sites at the same time had been hacked, and Westhost had a lot of work to do. Luckily they do daily backups of the site and the next afternoon I was back online with a version of my site that was as current as possible.
This is the effect the hack had on my traffic:
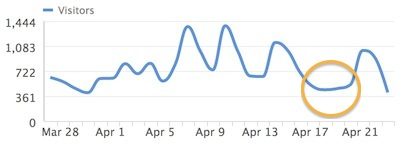
To put the above chart in perspective, that week's traffic was down ~ 30% compared to the prior week. In theory, that meant a 30% drop in revenue.
It's fair to say that I was eager to ensure (to the best of my abilities) that such a hack could not be repeated. I acted immediately.
My immediate steps
The first thing I did was verify that you had been following the steps outlined in my recent post on how to protect your WordPress website.
These were the absolute arguments: update my themes and plugins, make sure I have a recent backup, make sure my default profile is not named "admin", change my password, and check for security plugins on my site. With those items in place, it was time to move on.
I have no illusions that my site is now 100% secure; after all, there is no secure 100% site. Having said that, I know it is much more secure than before and will continue to investigate the site's security measures now and in the future. So far, this is what I have done.
1. I installed VaultPress
For those of you who don't know (* 5 *) VaultPress is a fully automated backup and security solution for WordPress. Is property of Automatic, the de facto "owners" of WordPress.
After having been using VaultPress for a few days, I can't believe I was so stingy that I didn't buy the service beforehand. Your basic package starts at $ 15 per month; I'll pay it for peace of mind any day of the week.
In fact, I chose to go with their Premium package ($ 40 per month) which includes:
- Real-time backup
- One-click automated site restoration
- Files, statistics and activity log
- Priority disaster recovery
- Priority "concierge" assistance
- Daily security scan
- Security notifications
- One-click fixers for security threats
- Site migration assistance
Basically, they have you covered.
Although VaultPress cannot ensure the security of your site against hackers, virtually can Ensure that your site can be restored relatively easily. There is something very relaxing about viewing hourly snapshots of your sites stored on VaultPress servers:
Even though there are many free backup solutions out there, I don't think anything beats the relative peace of mind I get from VaultPress. They have 90 snapshots of my site available to restore today, the most recent of which is only twenty minutes long. I know that my site is safe in your hands.
2. I managed my profiles
A hacker can access your site from any of the admin profiles within your WordPress backend, not just the your utilizar. Cuando cargué mis perfiles, pude ver que tenía otros tres perfiles: un perfil de póster invitado y otros dos perfiles para persons (confiables) a las que les había dado acceso a mi sitio.
I started by closing those two profiles and changing the role of the guest poster profile to Author. This is something I advise you to do: just create as many administrator profiles as absolutely necessary. At the same time, however, you need to ensure that each account is a suitable random and unique password and that those passwords are changed normally.
There are times when you will need to allow people (like your web designer) to access your site. In such situations, I advise you to create a profile for them with a new password and then delete that profile as soon as your need ends.
Always think about the entry points of your site and if they are strictly necessary.
3. I changed my passwords
You may think this was an obvious move, but in fact I'm not talking about my WordPress passwords. Even though I made change them, at the same time I was sure to change all passwords to particularly sensitive accounts, put another way:
If you're wondering why I made this move, just consider the story of Mat Honan, whose entire digital life was destroyed by hackers who originally hacked into his Amazon account. If you are in any way indifferent about online safety, then the above article is a must-read.
Considere esta cadena simple: un pirata informático obtiene acceso a su cuenta de correo electrónico desde la cual envió recientemente un correo electrónico a su diseñador web con los detalles de inicio de sesión para su sitio de WordPress. Eso es todo lo que necesitan para acceder a su sitio y hacer lo que quieran. To hack puede ser así de elemental.
4. I upgraded to SFTP
Aquí hay algo que tal vez no sepa: cualquier dato que transfiera por medio de de FTP (incluido su nombre de Username y contraseña) está completamente sin cifrar. Por lo tanto, cualquier persona que pueda interceptar transferencias FTP con éxito podrá recoger sus datos de inicio de sesión y acceder a su cuenta.
This not only makes it possible for them to add and remove files as they see fit, but at the same time they can access your WordPress database via phpMyAdmin and ultimately log into your site.
Simply put, it doesn't matter how secure direct access to your WordPress site is if hackers can get in via FTP. As such, I recommend that you disable FTP access to your site and transfer files using the alternate SFTP protocol, which make encrypt data. Any good hosting provider should be able to help you with this.
Speaking of hosting providers ...
5. Consider the suitability of your hosting solution
Me alegro de estar con Westhost. Fue su cortafuegos ModSecurity el que detectó el ataque en primer lugar y cerró mi sitio antes de que se pudieran producir daños graves. Al mismo tiempo realizan copias de seguridad diarias automáticas (que se utilizaron para restaurar el sitio) y cuentan con un excelente soporte al client para arrancar.
¿Puede decir lo mismo de su proveedor de alojamiento? Hay tantas opciones excelentes que sería una locura quedarse con un proveedor con el que no está satisfecho. Puede considerar cambiar a una de las soluciones de alojamiento administrado (como WPEngine) como lo hizo R Digital marketing recientemente.
Whatever your choice, be sure to ask about the security measures they take. Please consider the measures I have previously taken and make sure they are compatible with your hosting solution.
The moral of the story is this: don't compromise on security. Ultimately, keeping your site secure is more important than anything más. No tiene sentido tener un gran contents o un diseño nuevo y espectacular si nadie puede verlo debido a que su sitio ha sido destrozado por hackers despiadados.
The nefarious guys who have nothing better to do with their lives than hacking into people's sites aren't going away any time soon. The sooner you accept it and take reasonable steps to protect your site from attack, the better the long-term security of your online assets.
I would love to hear what you think of the steps I have taken. Are there any additional recommendations I would make? Let us know in the comment section!






