What is SafeBrowsing.biz?
SafeBrowsing.biz It is often called a browser hijacker because it takes control of the web browser and does things you may not want to do, such as changing your current search engine or setting a particular web page as the default home page. Many people basically call it a virus or malware. Security professionals generally call it a "PUP" or potentially unwanted program. Users who are victims tend to have less polite names for themselves.
SafeBrowsing.biz comes bundled as part of several other applications and add-ons. In some cases, the "typical" installation already includes the plugin and the only way to disable it is to use the "custom" installation, which many users will not do.
SafeBrowsing.biz Details
- Name of the browser hijacker: SafeBrowsing.biz
- Risk level: Means, medium
- Discovery date: 18/09/2016
- File length: Unknown
- Subtype: Browser hijackers
- Category: Browser hijackers
SafeBrowsing.biz aliases
SafeBrowsing.biz is also known by these other aliases:
- MacOS: MacInst-D
- potentially harmful program OSX/InstallCore
- Application.MAC.OSX.InstallMiez.DA
- Tool.Mac.ExtInstall.4
- OSX/ExtInstallTool.C potentially unsafe application
- Application.MAC.OSX.InstallMiez.DA
What are browser hijackers?
A browser hacker is a malicious program that changes web browser settings without the user's permission and redirects them to websites they did not want to visit. Usually called browser redirect viruses because they redirect the browser to other websites, usually malicious, a hacker is used to hack the browser.
A browser hijacker like SafeBrowsing.biz can change the default search engine or home page of the browser, slow down the loading of web pages, install various toolbars on the browser without the user's permission, and generate various contextual warnings for advertisements. .
The purpose of a browser hijacker is to help cybercriminals generate fraudulent advertising revenue. As an example, a browser redirects the victim's home page to the hijacker's search page, then the hijacker redirects the victim's search requests to links the hijacker wants to show the victim instead of legitimizing the results. from the search engine. When the user clicks on the search results, the hijacker is paid. The cybercriminal can also sell information about victims' browsing habits to third parties for marketing purposes.
A browser hijacker may contain spyware that makes it possible for the attacker to obtain the user's bank details or other confidential information. Browser hijacker malware can also install ransomware, malware that encrypts data on the victim's system and holds it hostage until the victim pays a sum of money to the hijackers to unlock it.
How did SafeBrowsing.biz get to my computer?
Generally, SafeBrowsing.biz can enter your computer in two ways. In the first case, you will be tempted to install them through malicious links exchanged by email, instant messaging or some web pages.
In the second method, they are provided with real software that is otherwise superbly functional and usable, but if you install it on your computer, you also install the pirated browser with it. It affects both Chrome, Firefox and IE Edge browser.
Symptoms of SafeBrowsing.biz?
Here are some typical signs that you have SafeBrowsing.biz on your system:
- Your browser's search engine will be modified without your consent.
- The home page of your web browser has mysteriously changed without your consent.
- The web pages you visit often do not display correctly.
- New toolbars, extensions or add-ons suddenly fill your browser.
How to remove SafeBrowsing.biz?
Some antivirus programs warn users about the presence of SafeBrowsing.biz browser hijacker, but some new hijackers may not be detected or the security software may not be able to remove the intruder. In these cases, users will need to reinstall their browser to regain control of the user interface.
In extreme cases, the hijacker reinstalls itself on the browser and users may need to delete the contents of their computer, install a new operating system and the latest browser version, and restore their personal files from a backup.
Method 1: Remove suspicious and unnecessary toolbars and extensions. They can be reinstalled, so it may be wise to delete everything. Then close your browser and restart your computer.
Once your computer has restarted, make sure what you deleted is still gone. If so, change your browser settings (default search engine, home page, etc.) to ensure that what you have deleted is always gone. - and everything will return to normal. If you are still being redirected or if an extension is not uninstalled, you should continue.
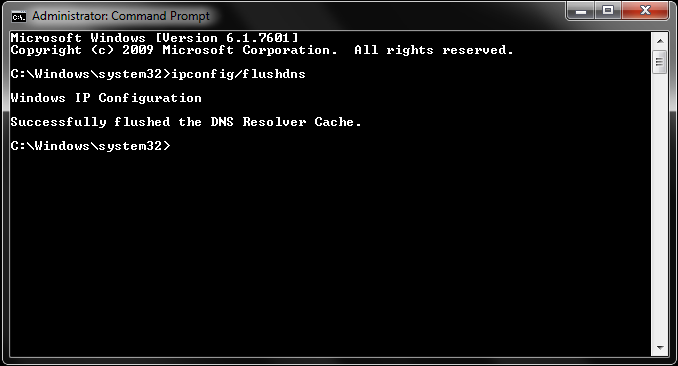
Method 2: Clear the DNS cache. In Windows, you need to open the command prompt and type the following:
ipconfig / flushdns
- Press “enter” and clear the DNS cache. You will then see “Windows IP settings successfully cleared the DNS resolver cache”.
- Clearing it will restore DNS redirects to your network settings.
Method 3- Browse the Add or Remove Programs section and remove the apps connected to the browser hacker. If you don't see something, be sure to scan it before deleting, preferably on a non-infected device.
Restart the computer and verify that the problem is resolved.
Method 4: Check your proxy settings again. Some hackers can even modify the Internet server you use to connect to the Web. Basically removing the malware or the malware itself doesn't change anything, so it's an important step in restoring your computer.
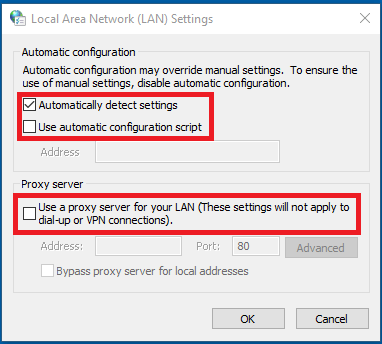
- To access your proxy settings, first go to Control Panel, then Network and Internet, then Internet Options.
- In the Internet Options menu, go to the Connections tab. Press the LAN Settings button.
- Make sure that the automatic detection setting is enabled and that the other two options "Use automatic configuration script" and "Use proxy server for your LAN" are not empty.
conclusion
Browser hijacking is common, and in several cases, users are unaware that their browser is infected with some malware.
In this way, it is essential to always read the steps of the installation procedure carefully and check any unexpected boxes that may be checked by default. At the same time, never open URLs or attachments in emails you don't trust.
Additionally, caution should be exercised with browser extensions, as many browser extensions are generally outdated and are therefore misused by hackers for fraudulent activities. Hackers themselves design browser extensions to later infect them with malicious scripts.
Whenever you are browsing the web and are prohibited from visiting a web portal, and Google's safe browsing listing appears with a warning message, it is best not to ignore it and visit the site altogether.
The good news is that browser hacking doesn't have to happen to you now that you know what it is. Remember these methods to avoid it, and you won't fall for fraudulent scammers!